In the high-octane world of crypto, decentralized autonomous organizations (DAOs) have been making waves. The vibes seem to be great. But let’s get real, it’s not all sunshine and rainbows. Remember that infamous DAO hack back in Ethereum’s history books? A single error in code that cost 3.6 million ETH (equivalent to 8.7 billion USD as of Feb 8, 2024)? Yeah, it was a wild ride and a lesson for the ages. Fast-forward seven years, and while DAOs are on the rise, hacks and exploits seem to be the annoying party crashers happening every month.
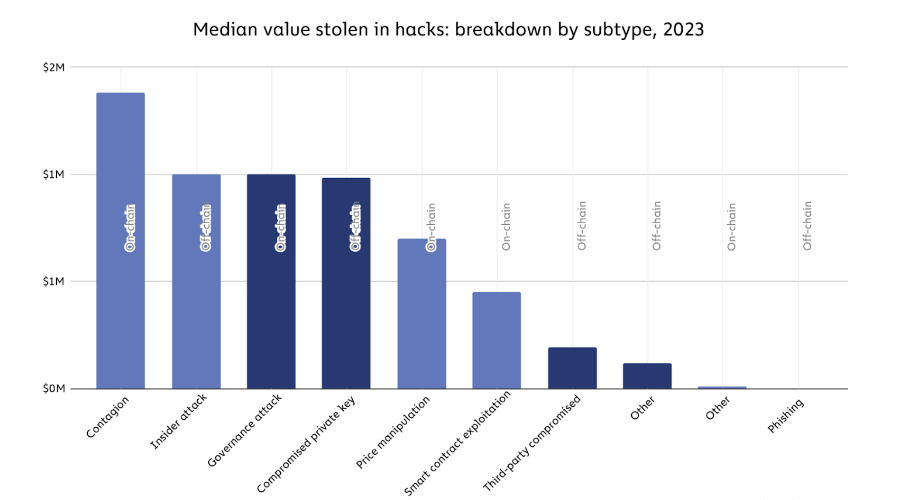
In 2023, the collective sum siphoned off from DeFi protocols stood at a substantial $1.1 billion, as reported by Chainalysis. This figure marks a notable 64% decline compared to the staggering $3.1 billion vanishing act we witnessed in 2022. But make no mistake: the decline is mainly due to decreasing crypto prices, not a reduction in the number of attacks. The overall security situation has not improved.
One cause for concern: while “governance attacks” only make up a fraction of total hacks, their share has been increasing in recent years. And when it comes to the median value stolen, governance attacks score highly. Plus: governance hacks as reported by Halborn only capture direct abuse of governance processes. But most types of hacks can be traced back to bad governance: insider attacks, price manipulation and smart contract exploits all thrive in protocols with lax governance.
The Governance Gamble
Sure, the intended benefits of DAO governance include efficient capital allocation, leading to motivated members and empowered stakeholders, all while protecting against fraud. But here’s the thing: poor governance can make things even worse.
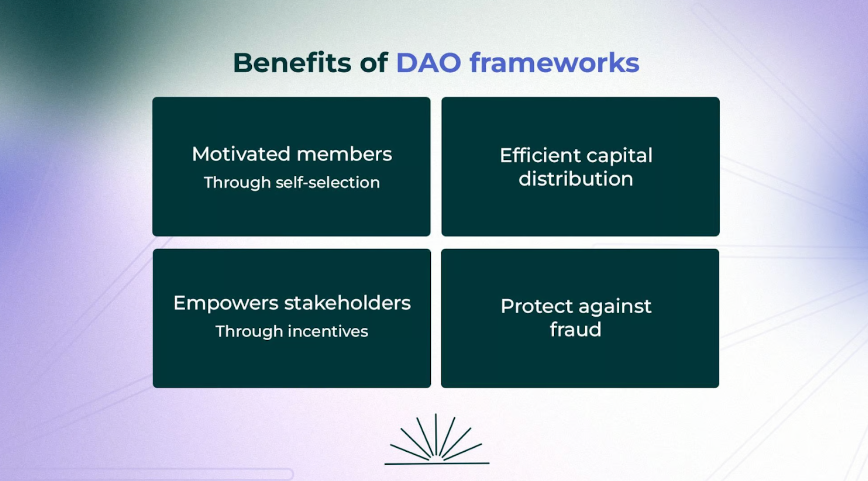
Major DAO governance challenges
Decentralized Notifications
These are a headache waiting to explode. If some sneaky attacker can block those notifications, they can slip in some shady proposals right under the radar. Imagine a party where the bouncer is napping, and the gatecrashers are having a field day. But what happened to Tornado Cash is beyond imagination: an attacker proposed a contract identical to the previously passed proposal, but with a self-destruct function that went unnoticed. After getting accepted, the hackers granted themselves 1.2 million votes – much more than the rest of legitimate members – while stealing around 1 million dollars in crypto assets. There were no checks and balances in Tornado Cash’s governance to prevent this.
Playing with Fire in Complex Multicalls
DAO proposals often get all tangled up in complex multicall transactions that allow to either exchange several assets simultaneously, amplify individual voting power, or use delegated treasury voting power to get more tokens. It’s like a game of Jenga, but instead of fun, it’s high-stakes crypto. If the DAO isn’t big on auditing and scrutinizing these proposals, bad actors can exploit this chaos to push through complicated proposals that could blow up in everyone’s faces. See the smart contract exploits below.
Configuration Conundrums
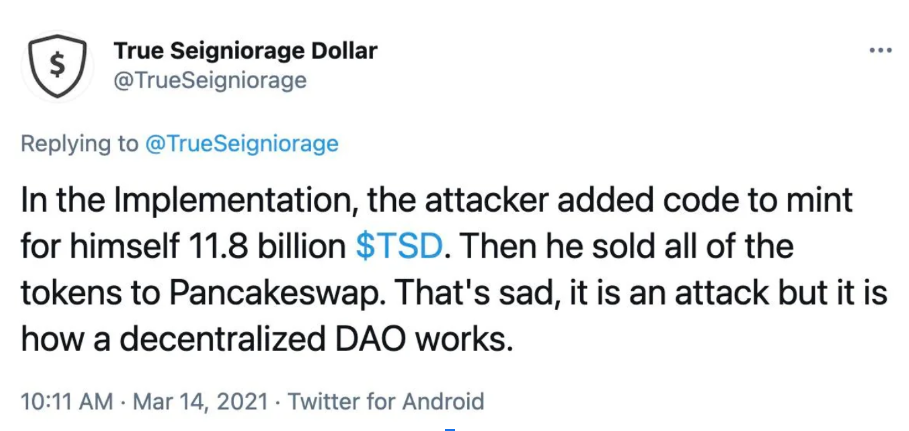
Oh boy, misconfigured DAOs are like open invitations for troublemakers. Wrong thresholds, messed-up timelocks – it’s like leaving your front door wide open for burglars. And let’s not even talk about poorly thought-out incentives with a side of unexpected disasters that can turn a well-intentioned token into a hot mess. One example would be TrueSeigniorageDollar. A hacker gained control of the DAO’s voting process by acquiring a 33% stake in it. They then proposed and passed code changes using their stake, allowing them to print 11.8 billion TSD tokens with malicious code. The hacker dumped these coins on PancakeSwap, crashing the project’s price to zero instantly.
Spamming the Party
Spam is the unruly guest that just won’t leave the party. Especially on gasless sidechains where there are no penalties for spamming. Picture this: someone drops a whopping 50,000 proposals on a DAO. Frontend systems get a migraine, and sorting the good from the bad becomes a crazy puzzle. Chaos reigns, and the bad ideas slip through the cracks. Here’s one user explaining “how to use $34,000 to conduct a spam proposal attack on NNS” (Network Nervous System that controls the Internet Computer blockchain).
Decentralization Dilemmas
Achieving true decentralization is like trying to herd cats, especially for small or budding DAOs. They are vulnerable to governance attacks, where some slick operators borrow a ton of governance tokens to muscle their proposals to the front. It’s like trying to pull off a heist, crypto-style. And if the community is tight-knit, it’s “game on” for behind-the-scenes deals. That’s what happened to Beanstalk when “a malicious governance proposal was pushed through by a flash loan, and the attacker then voted to transfer all the assets to themselves,” just over $181 million.
The Apathy Epidemic
Member apathy is like the sneaky enemy no one sees coming. From sloppy proposal reviews to a dwindling sense of decentralization, it’s a recipe for disaster. DAOs are essentially a tech-human mashup. Humans can be messy and chaotic, while technology (smart contracts, anyone?) demands precision and logic. If the community leans too heavily on a few leaders, it’s a ticking time bomb. This is what has been happening to Polkadot lately, but who are we to judge?

Smart contracts exploit DAO governance
Moreover, there are at least a dozen ways to exploit governance due to imperfect rules, whether on the system-level design or within the code details. Here’s a profound list of DeFi audits by Dacian that prevented possible hacks using breaches in DAO governance:
- Using flash-loans to decide proposals (Cyfrin’s DeXe Protocol, Beanstalk, MakerDAO)
- Destroying user voting power (Golom)
- Amplifying individual voting power by reducing total voting power (FrankenDAO)
- Using proposal creation for incorrect total voting power before a snapshot (Cyfrin)
- Impossible to reach quorum (PartyDAO)
- Using delegated treasury voting power to get more (Cello)
- Bypassing voting restrictions via delegation (Cyfrin)
- Voting With Same Tokens Multiple Times (Nouns Builder)
- Making voting tokens forever locked in proposals without deadlines (Olympus DAO)
- Letting anyone pass proposals before DAO mints voting tokens (Olympus DAO)
- Steal tokens from token sale proposal (Cyfrin)
- Bypassing token sale max allocation per user (Cyfrin)
As he summarized well, “on-chain DAO Governance protocols create a large attack surface for creative exploitation.” Unfortunately, it is true. Below are just a few cases.
It’s time to reevaluate and realign for a more robust and resilient future.
Q Protocol Has a Solution for Your DAO
In dozens of cases above, we’ve seen how often code and the system design itself happen to be flawed. Both people and algorithms are prone to attacks. This is why the Q Protocol entered the scene: to unite the strengths of public, open, and decentralized ledgers with the reliability of enforceable private contracts through its visionary governance framework. Q’s mission is to unleash a new era of decentralized decision-making beyond “code-is-law.” Here’s how.
Q Governance: a missing piece
One of the lessons we can learn from the cases above is the need to borrow wisdom from political science and established organizational and institutional design principles. Q utilizes real-life concepts such as:
The Constitution
The Q Constitution serves as the governing document for Q, clearly outlining the rights and responsibilities of all stakeholders. Unlike many other projects that rely on implicit rules and goodwill, Q distinguishes itself by enforcing its Constitution through on-chain and off-chain mechanisms, turning it into a legally binding contract akin to real-world agreements;
Dispute Resolution
Q has integrated the Rules of Arbitration of the International Chamber of Commerce (ICC Rules) for its Private arbitration function;
Expert panels
As we observed earlier, DAOs are susceptible both to online voting flaws and physical key administration risk. Q governance relies on expert panels that introduce professionalism to technical decisions while countering the decision fatigue of QGOV token holders;
Economic incentives
Q has separated incentives for 4 groups of participants: Validator Nodes, Root Nodes, Q Token (QGOV) Holders, Q ID Holders.

Here’s the interesting part for DAOs: Q’s governance framework does not only apply to the core protocol itself; it can also be used by DAOs or other protocols. Through Q’s concept of “Shared Governance Security”, decentralized organizations can opt in for “governance-as-a-service.” It is meant to improve their governance while reducing the effort required by DAO members.
The concept includes three standardized opt-in features:
- protected code,
- expert decision-making,
- and treasury oversight,
and will assist with facilitating decentralized code upgrades, protecting against centralization, and ensuring proper treasury spending. Web3 projects, such as Q Name Service and DeSci World, are already utilizing these features to enhance their governance structures and security.
Ready to improve the governance of your DAO or launch a new one? Explore this page: https://q.org/build
Also read:
Join the community on:






Leave a Reply